I’ve been using GoDaddy VPS servers for a few years now and they’ve been OK up until Godaddy Server number 5.
I currently have two Godaddy VPS servers online, a 2GB Centos 6 VPS and a 3GB Centos 6 VPS.
I’m in the process of reducing the size of my network of domains (currently over 100 domains), pretty much plan to let anything not making much money to expire and concentrate on a core set of profitable domains (probably around 50 domains: too much hassle managing 100+). I should only need one VPS server for around 50 domains, though want to upgrade the RAM to 4GB.
Update: currently have a Godaddy VPS (I did reduce the size of my network to around 50 domains).
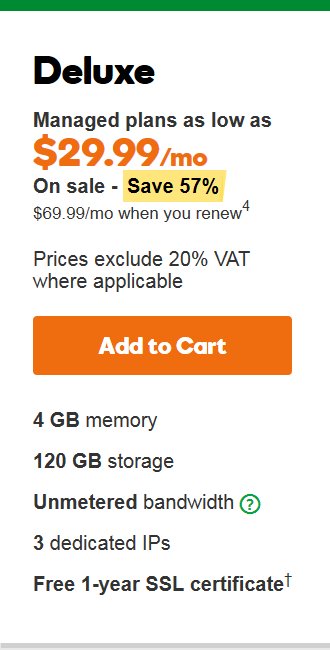
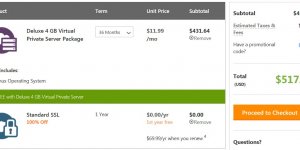
Godaddy Deluxe 4 GB Virtual Private Server Specifications
Back in 2016 it was cheaper to buy a new Godaddy Deluxe 4 GB VPS server plan than pay for upgrades to an old server, also a new server will probably have newer components and the option for more recent versions of Linux (I wanted Centos 7, PHP 7 etc…).
4 GB memory
120 GB storage
Unmetered bandwidth
3 dedicated IPs (though only 1 IP if you select unmanaged!).
Free 1-year SSL certificate
$29.99 a month (paid 12 months in advance) if managed
$19.99 a month (paid 12 months in advance) if unmanaged
On sale – Save 57%
$69.99 a month when renewed
I’m in the UK, so 20% VAT :-(
It’s cheaper than the 3GB Godaddy VPS I currently pay for.
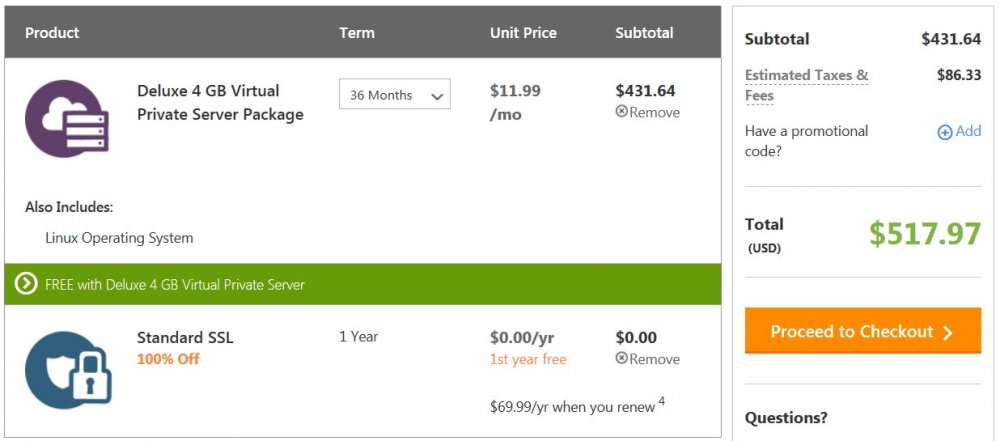
Hmm, just realized they overcharged me!
I was charged
Deluxe 4 GB Virtual Private Server – 1 Year: $479.88 USD (~$40 a month)
VAT: $95.98 USD
Total Amount: $575.86 USD
Should have been
Deluxe 4 GB Virtual Private Server – 1 Year: $239.88 USD (~$20 a month)
VAT: $47.98 USD
Total Amount: $287.86 USD
Godaddy VPS Setup Problems : It All Went Wrong With Centos 7
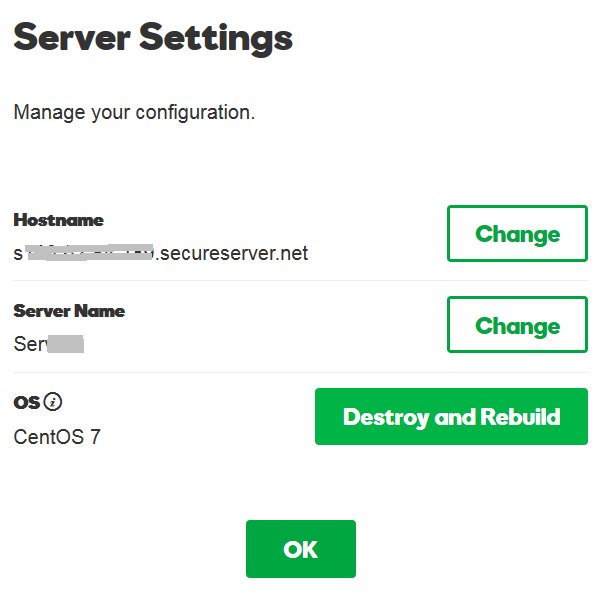
Anyway, got access to the server quite quickly (no issues with that) and the server had an awesome Destroy and Rebuild feature.
Which meant in a space of 10 mins if you messed up you could start again from scratch and even choose a different version of Linus: Centos 6, Centos 7, Fedora 23 (I think) and a version of Ubuntu.
I’m familiar with Centos, so tried Centos 7 and 6 only.
I use the control panel Virtualmin, so after a quick “Yum Update” command to update the server to the latest version of Centos 7 I installed Virtualmin: done this at least half a dozen times before with other servers, it’s easy.
Unfortunately that’s when the problems began.
Important information: the server starts with all ports closed other than ports 22 (SHH access) and port 80 (HTTP access). To access other services you need to manually open ports using iptables and/or firewalld.
I couldn’t log in to Virtualmin because port 10000 was closed (Virtualmin opens this port via iptables/firewalld at installation). Weirdly port 20000 (Usermin: part of Virtualmin) and some other ports (MYSQL and others) were open, though others you’d expect to open during a Virtualmin install (POP3 and FTP for example) are closed. Didn’t figure out how Virtualmin opened those ports with iptables not active and firewalld disabled.
After a LOT of research and Destroying and Rebuilding the server over half a dozen times tracked the issue down to the server being run under an OpenVZ container and this can cause problems with iptables/firewalld.
The Godaddy Deluxe 4 GB VPS server started with iptables NOT setup correctly, it was enabled at boot (so it tried to run), but failed to activate due to an error on line 14 of the default iptables file (line 14 was the commit line). I could get iptables to activate by saving iptables with no default rules, but no matter what I tried I couldn’t open a single port via iptables (or firwalld, tried them both).
The problem is this line within the default iptables file:
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPTwhen trying to add this rule manually via
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPTThe result it:
iptables: No chain/target/match by that name.
I’m far from a server expert, I can manage the day to day running of a dedicated server with no major problems (being managing dedicated servers and VPS servers for over a decade), I can fix server problems as long as I can find the solution online. I hate using the command line, so most of my server activity has been under a control panel (Virtualmin), with this issue it was ALL command line as I couldn’t get Virtualmin to run, so made progress slower.
Wasted days trying to get iptables and/or firewalld to work with no joy.
Three Godaddy support requests, first I got someone who knew nothing about servers, second knew about servers and offered to charge $80 to setup iptables or a link to an article on using iptables.
Third I Destroyed and Rebuilt the server (so was a fresh server, I changed nothing so Godaddy support could check the server at the initial setup stage). I was on support for over an hour, he said his admin was looking at the server, but based on the responses I don’t think they did anything: end result was I cancelled the server and asked for a full refund: still waiting on the refund, apparently takes 3-7 days to make a refund at Godaddy (update: I got the refund).
Clearly the default server setup was faulty. Iptables and/or firewalld should be enabled AND active at first boot (iptables was enabled, but not active) since they are required to manage ports. Either Godaddy support couldn’t or wouldn’t activate iptables.
Godaddy support is next to useless for anything difficult in my experience.
Update: got it working by selecting the Centos 6 version. I would have rather gone with Centos 7, but nothing I tried worked. See my GoDaddy VPS Review for that VPS server.
David Law
Dedicated Server Reviews
Used a number of companies for dedicated servers between 2005 and 2019, here they are in chronological order. The last link is the review of the company I’m using in 2019.









I’m having this issue with a new Centos 7 VPS and looks like it’s to do with the OpenVZ container.
The server starts with all ports except 22 and 80 closed and iptables enabled, but NOT active because the default iptables file (/etc/sysconfig/iptables/) fails on line 14 (the commit line). This is the entire file:
# sample configuration for iptables service# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
there's a blank line here
The COMMIT line is line 14, but I’ve tried adding commit between each rule (after each -A INPUT” rule) and it fails at the first rule.
Can only get iptables to run via the “service iptables save” command which results in iptables running, but no rules saved.
# iptables -S-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
The weird thing is ports 22 and 80 are open even when iptables is disabled at boot or has no rules.
I’ve tried disabling iptables and rebooting and ports 22 and 80 are still open, everything else blocked.
Firewalld wasn’t installed, after disabling iptables and installing firewalld
# sudo firewall-cmd --statenot running
and
# firewall-cmd --set-default-zone=publicWarning: ZONE_ALREADY_SET: public
success
and
# sudo systemctl status firewalld -l
� firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2016-12-30 17:49:36 UTC; 14min ago
Docs: man:firewalld(1)
Main PID: 698 (firewalld)
CGroup: /system.slice/firewalld.service
��698 /usr/bin/python -Es /usr/sbin/firewalld --nofork --nopid
Dec 30 17:49:36 s######.secureserver.net firewalld[698]: WARNING: ipset not usable, disabling ipset usage in firewall.
Dec 30 17:49:36 s######..secureserver.net firewalld[698]: WARNING: ip6tables not usable, disabling IPv6 firewall.
Dec 30 17:49:36 s######..secureserver.net firewalld[698]: WARNING: '/usr/sbin/iptables-restore -n' failed:
Dec 30 17:49:36 s######..secureserver.net firewalld[698]: WARNING: '/usr/sbin/ebtables-restore --noflush' failed:
Dec 30 17:49:36 s######..secureserver.net firewalld[698]: ERROR: COMMAND_FAILED
Dec 30 17:50:41 s######..secureserver.net firewalld[698]: ERROR: ZONE_ALREADY_SET: public
The "sudo ifconfig" command outputs "sudo: ifconfig: command not found"
At this point I’m stuck.
I know iptables isn’t working as it should and firewalld when installed says it’s not running.
To confuse things even further I’m trying to install Virtualmin and it installs and opens ports for MYSQL and Usermin (port 20000), but fails to open other ports for Webmin (10000), POP3, FTP…
Godaddy support are useless, they don’t appear to understand the concept that the server is starting with a fault in the iptables setup.
What I’d really like to know is how ports 22 and 80 are open when iptables and firewalld aren’t enabled? Is there another firewall built into Godaddy servers by default???
There’s also some info about the iptables issue at https://www.centos.org/forums/viewtopic.php?f=51&t=54469
David Law
How to Open Ports on a Godaddy VPS Server Running Centos 7 OpenVZ
I think the new Godaddy VPS hates me.
Figured out why iptables was throwing out an error on line 14 as a freshly built server: I’d made no changes to the server.
The Godaddy Deluxe 4 GB Virtual Private Server which is run under an OpenVZ container (one of the ways a dedicated server is partitioned into multiple VPS servers) starts with all ports closed other than ports 22 (SHH) and port 80 (HTTP).
This means the server is secure, but requires ports opening to use other services like email, MYSQL and a control panel: for example Virtualmin needs amongst other ports, port 10000 and port 20000 open to function.
So a firewall management program should be installed with the server to manage ports.
Iptables is installed and enabled, so should activate at boot, but does not activate due to an error on line 14.
Ip6tables is installed and disabled (turned off).
Firewalld (a more recent firewall sometimes installed with Centos 7) is not installed.
As far as I can tell iptables is the only way to manage ports on the Godaddy VPS running Centos 7.
The line 14 iptables error was caused by Godaddy not enabling multiple iptable kernal modules. These should be installed under the OpenVZ hardware node which Godaddy customers have no access to.
According to https://forum.configserver.com/viewtopic.php?f=6&t=212 the required iptables modules for full iptables support are:
ip_tablesipt_state
ipt_multiport
iptable_filter
ipt_limit
ipt_LOG
ipt_REJECT
ipt_conntrack
ip_conntrack
ip_conntrack_ftp
iptable_mangle
Other iptables modules for additional functionality:
ipt_owneript_recent
iptable_nat
ipt_REDIRECT
I installed ConfigServer Security & Firewall (CSF) for testing and according to the “/etc/csf/csftest.pl” test, the Godaddy VPS Server is missing at least these modules:
ipt_state/xt_statext_connlimit
iptable_nat/ipt_REDIRECT
iptable_nat/ipt_DNAT
The earlier forum post about modules required for CSF to function is from 2007, I assume there’s new iptables modules since then.
Anyway, I confirmed the missing iptables modules by trying to add this iptables rule:
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPTOutput:
iptables: No chain/target/match by that name.
Indicates a module is missing, specifically the state module.
I contacted Godaddy support, explained I wanted the iptables modules enabled and Godaddy support enabled them, yeah :-)
Iptables now activated at boot so iptables should work as expected.
Tried installing Virtualmin and guess what, it still didn’t work!!!!
Port 10000 was still closed, port 20000 was open, the same result as before enabling the missing modules!
After a lot of testing with ConfigServer Security & Firewall I was still no closer to figuring this out and was making a bit of a mess, so decided to start from scratch again. I Destroyed and Rebuilt the VPS server AGAIN to start with a fresh Centos 7 installation and now the enabled iptable modules are no longer enabled!!!!
Godaddy Support You Are a bunch of Idiots
I don’t know much about managing OpenVZ, but would assume there’s an option to set the iptables modules to survive a rebuild: if not Godaddy support should have told me the new settings won’t survive a rebuild.
They are a bunch of bloody idiots at Godaddy.
They can’t setup a VPS which works without modifying the server: the support person I dealt with said he has to deal with the missing iptables modules roughly twice a week!
Most of Godaddy support don’t have a clue, you’d have better support asking your pet cat how to fix an issue.
After all this hassle I’m still not sure why port 10000 (and others) won’t open, but port 20000 (and others) will via iptables.
Just to make things more interesting. With the fresh Centos 7 server I disabled and masked iptables/ip6tables so there wouldn’t be any program managing firewall rules. That’s the theory anyway.
Here’s the output for the relevant commands:
# sudo systemctl is-enabled iptables
masked
# sudo systemctl is-enabled ip6tables
masked
# sudo systemctl is-enabled firewalld
Failed to get unit file state for firewalld.service: No such file or directory
With a fresh server ports 22 and 80 are still open all other ports I’ve tested are listed as closed.
Testing ports via: http://ports.my-addr.com/check-all-open-ports-online.php
Ports Tested :20,21,22,25,53,80,110,111,143,443,465,587,993,995,2222,2525,3306,10000,10001,10002,10003,10004,10005,20000
Fresh server with iptables/ip6tables disabled/masked: no control panel installed.
20/tcp closed ftp-data21/tcp closed ftp
22/tcp open ssh
25/tcp closed smtp
53/tcp closed domain
80/tcp open http
110/tcp closed pop3
111/tcp closed rpcbind
143/tcp closed imap
443/tcp closed https
465/tcp closed smtps
587/tcp closed submission
993/tcp closed imaps
995/tcp closed pop3s
2222/tcp closed EtherNet/IP-1
2525/tcp closed ms-v-worlds
3306/tcp closed mysql
10000/tcp closed snet-sensor-mgmt
10001/tcp closed scp-config
10002/tcp closed documentum
10003/tcp closed documentum_s
10004/tcp closed emcrmirccd
10005/tcp closed stel
20000/tcp closed dnp
The above is as expected.
After installing Virtualmin before a reboot:
20/tcp closed ftp-data21/tcp closed ftp
22/tcp open ssh
25/tcp open smtp
53/tcp closed domain
80/tcp open http
110/tcp closed pop3
111/tcp open rpcbind
143/tcp closed imap
443/tcp open https
465/tcp closed smtps
587/tcp open submission
993/tcp closed imaps
995/tcp closed pop3s
2222/tcp closed EtherNet/IP-1
2525/tcp closed ms-v-worlds
3306/tcp open mysql
10000/tcp closed snet-sensor-mgmt
10001/tcp closed scp-config
10002/tcp closed documentum
10003/tcp closed documentum_s
10004/tcp closed emcrmirccd
10005/tcp closed stel
20000/tcp closed dnp
Either before or after a reboot I think all these ports should be open.
After installing Virtualmin after a reboot:
20/tcp closed ftp-data21/tcp closed ftp
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp closed http
110/tcp closed pop3
111/tcp open rpcbind
143/tcp closed imap
443/tcp closed https
465/tcp closed smtps
587/tcp open submission
993/tcp closed imaps
995/tcp closed pop3s
2222/tcp closed EtherNet/IP-1
2525/tcp closed ms-v-worlds
3306/tcp closed mysql
10000/tcp closed snet-sensor-mgmt
10001/tcp closed scp-config
10002/tcp closed documentum
10003/tcp closed documentum_s
10004/tcp closed emcrmirccd
10005/tcp closed stel
20000/tcp open dnp
Why has MYSQL closed? Port 20000 (Usermin) is open, port 10000 (Webmin) is closed!!!
From the Virtualmin log file:
Configuring firewall rulesAllowing traffic on TCP port: ssh
Allowing traffic on TCP port: smtp
Allowing traffic on TCP port: submission
Allowing traffic on TCP port: domain
Allowing traffic on TCP port: ftp
Allowing traffic on TCP port: ftp-data
Allowing traffic on TCP port: pop3
Allowing traffic on TCP port: pop3s
Allowing traffic on TCP port: imap
Allowing traffic on TCP port: imaps
Allowing traffic on TCP port: http
Allowing traffic on TCP port: https
Allowing traffic on TCP port: 2222
Allowing traffic on TCP port: 10000
Allowing traffic on TCP port: 10001
Allowing traffic on TCP port: 10002
Allowing traffic on TCP port: 10003
Allowing traffic on TCP port: 10004
Allowing traffic on TCP port: 10005
Allowing traffic on TCP port: 20000
Allowing traffic on UDP port: domain
Allowing traffic on UDP port: ftp
Allowing traffic on UDP port: ftp-data
Contents of the “/etc/sysconfig/iptables” file:
# sample configuration for iptables service# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:FORWARD ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -p udp -m udp --dport ftp-data -j ACCEPT
-A INPUT -p udp -m udp --dport ftp -j ACCEPT
-A INPUT -p udp -m udp --dport domain -j ACCEPT
-A INPUT -p tcp -m tcp --dport 20000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10005 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10004 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10003 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10002 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10001 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 2222 -j ACCEPT
-A INPUT -p tcp -m tcp --dport https -j ACCEPT
-A INPUT -p tcp -m tcp --dport http -j ACCEPT
-A INPUT -p tcp -m tcp --dport imaps -j ACCEPT
-A INPUT -p tcp -m tcp --dport imap -j ACCEPT
-A INPUT -p tcp -m tcp --dport pop3s -j ACCEPT
-A INPUT -p tcp -m tcp --dport pop3 -j ACCEPT
-A INPUT -p tcp -m tcp --dport ftp-data -j ACCEPT
-A INPUT -p tcp -m tcp --dport ftp -j ACCEPT
-A INPUT -p tcp -m tcp --dport domain -j ACCEPT
-A INPUT -p tcp -m tcp --dport submission -j ACCEPT
-A INPUT -p tcp -m tcp --dport smtp -j ACCEPT
-A INPUT -p tcp -m tcp --dport ssh -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state -m tcp --dport 22 --state NEW -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
It would appear another program is managing the firewall since iptables/ip6tables is masked and not all the above rules are working.
I’m completely confused?
David
Installing Virtualmin On Centos 7 with Iptables/Ip6tables Disabled
Finally figured it out.
Still haven’t a clue how the ports are opening etc… with iptables/ip6tables disabled (masked) in Centos 7, but I got it working.
I wasn’t having any luck with opening the Webmin port 10000, so gave up.
Switched Webmin to use another port, first downloaded the “/etc/services” file to find an unused port. The services file lists all named ports, picked one not in the file.
Downloaded the “/etc/webmin/miniserv.conf” file and changed to two instances of
port=10000listen=1000
To use the selected port (changed 10000 to another port number), uploaded it back to the server, rebooted and found Webmin wasn’t running: wasn’t running before this, but I get caught up with opening port 10000 so didn’t investigate.
Both of these commands said Webmin had stopped
service --status-allservice webmin status
Took a look at the error file and tracked down the issue to another setting in the “/etc/webmin/miniserv.conf” file.
Changed “ipv6=1” to “ipv6=0” and reuploaded, rebooted…
Also modified the “/etc/sysyconfig/iptables/” file to include the new port number. Basically added a new rule under the port 10000 rule (third line below replacing NEWPORTHERE with the port number 12345):
-A INPUT -p tcp -m tcp --dport 10001 -j ACCEPT-A INPUT -p tcp -m tcp --dport 10000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport NEWPORTHERE -j ACCEPT
-A INPUT -p tcp -m tcp --dport 2222 -j ACCEPT
-A INPUT -p tcp -m tcp --dport https -j ACCEPT
Don’t know if the above is important, since iptables/ip6tablesis disabled the file shouldn’t do anything (unless there’s another service managing the firewall).
Uploaded the iptables file, rebooted and Webmin now worked on the new port.
May well be a case I could have skipped pretty much all the above except the “ipv6=1” to “ipv6=0” change. I’d have to change it all back to be sure, think I’ll pass on that one :-) It’s also more secure to put Webmin on a port other than 10000.
Had some issues with the Virtualmin post setup, got this error when setting up the database:
An error occurred starting MySQL :
Redirecting to /bin/systemctl start mariadb.service
Job for mariadb.service failed because the control process exited with error code. See "systemctl status mariadb.service" and "journalctl -xe" for details
Checked the log file and tracked it down to a folder permission problem, this command fixed it:
chown mysql:mysql /var/run/mariadb/Looks like it’s finally working, not added a domain yet, so won’t be 100% certain until I install a Virtualserver.
Can not believe how long this took to fix, though on the plus side I’m around 100X more experienced at managing servers via a SHH program now :-)
David
Hello David
After following your journey, I am now very hesitant to destroy and rebuild my VPS server.I own 2 VPS and I am only having trouble with the 2G one. the 4G is working fine. I have been a full time affiliate now for 6 years. 3 days ago the 2G VPS opened up with the message You don’t have any sites.Create with WHM
Problem, cannot access cpanel or WHM. I need to restart mysql but cannot get access to do so.
I will keep researching but I thank you for your insightful review.